PJI11103-2016-2-felipe
Dário de Bordo
Projeto Integrador 3 2016/2
RADIUS - 27/10/16
AP
1. Configurado AP em Wireless Security para utilizar 'WPA/WPA2 - Enterprise';
2. Informado IP do servidor RADIUS 192.168.0.2 com a senha 1234;
Servidor
1. Instalado freeradius;
2. /etc/freeradius/clients.conf;
client 192.168.0.1 {
ipaddr = 192.168.0.1
shortname = AP
secret = 1234
nastype = other
}
</syntaxhighlight>
3. /etc/freeradius/users;
felipe Cleartext-Password :="#Pastel2016"</syntaxhighlight>
4. Ajustadas configurações dos parâmetros de log /etc/freeradius/radiusd.conf
log {
destination = files
file = ${logdir}/radius.log
syslog_facility = daemon
stripped_names = no
auth = yes
auth_badpass = yes
auth_goodpass = no
}
</syntaxhighlight>
5. LOG de acesso
Thu Oct 27 19:31:59 2016 : Info: Ready to process requests.
Thu Oct 27 19:32:43 2016 : Auth: Login OK: [felipe/<via Auth-Type = EAP>] (from client AP port 0 via TLS tunnel)
Thu Oct 27 19:32:43 2016 : Auth: Login OK: [felipe/<via Auth-Type = EAP>] (from client AP port 0 cli 10-C3-7B-A5-6B-AF)
</syntaxhighlight>
Servidores Operadora e Galpão
Em ambos os servidores foram configurados os APs sem DHCP nas interfaces LAN, com o ip 192.168.10.15 configurado para comunicação com o IP da VLAN 10 dos servidores.
No AP da Operadora ficou configurado como servidor RADIUS o IP 192.168.10.10.
No AP do Galpão ficou configurado como servidor RADIUS o IP 192.168.10.1.
Nas interfaces WAN dos APs (sem uso) ficou configurado o IP 192.168.0.1 para o caso de perda de acesso pelas interfaces LAN.
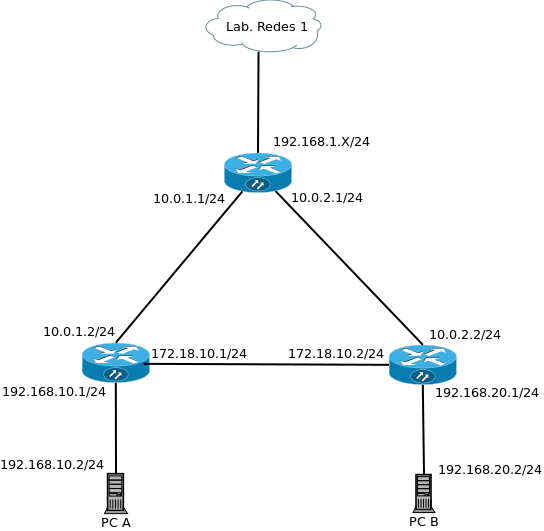
Roteamento estático - 17/11/16
Roteador Borda
eth0 - 192.168.1.111/24
eth1 - 10.16.1.1/24
eth2 - 10.16.2.1/24
Roteador 2
eth0 10.16.1.2/24
eth1 172.16.10.1/24
eth2 192.16.10.1/24
Roteador 3
eth0 10.16.2.2/24
eth1 172.16.10.2/24
eth2 192.16.20.1/24
</syntaxhighlight>
Tabelas de rotas
Roteador 2
aluno@ubuntu:~$ route -n
Tabela de Roteamento IP do Kernel
Destino Roteador MáscaraGen. Opções Métrica Ref Uso Iface
0.0.0.0 10.16.1.1 0.0.0.0 UG 0 0 0 eth0
10.16.1.0 0.0.0.0 255.255.255.0 U 0 0 0 eth0
172.16.10.0 0.0.0.0 255.255.255.0 U 0 0 0 eth1
192.16.10.0 0.0.0.0 255.255.255.0 U 0 0 0 eth2
192.16.20.0 172.16.10.2 255.255.255.0 UG 0 0 0 eth1
Roteador 3
aluno@ubuntu:~$ route -n
Tabela de Roteamento IP do Kernel
Destino Roteador MáscaraGen. Opções Métrica Ref Uso Iface
0.0.0.0 10.16.2.1 0.0.0.0 UG 0 0 0 eth0
10.16.2.0 0.0.0.0 255.255.255.0 U 0 0 0 eth0
172.16.10.0 0.0.0.0 255.255.255.0 U 0 0 0 eth1
192.16.10.0 172.16.10.1 255.255.255.0 UG 0 0 0 eth1
192.16.20.0 0.0.0.0 255.255.255.0 U 0 0 0 eth2
Operadora
aluno@ubuntu:~$ route -n
Tabela de Roteamento IP do Kernel
Destino Roteador MáscaraGen. Opções Métrica Ref Uso Iface
0.0.0.0 192.168.1.1 0.0.0.0 UG 0 0 0 eth0
10.16.1.0 0.0.0.0 255.255.255.0 U 0 0 0 eth1
10.16.2.0 0.0.0.0 255.255.255.0 U 0 0 0 eth2
192.16.10.0 10.16.1.2 255.255.255.0 UG 0 0 0 eth1
192.16.20.0 10.16.2.2 255.255.255.0 UG 0 0 0 eth2
192.168.1.0 0.0.0.0 255.255.255.0 U 0 0 0 eth0
</syntaxhighlight>
NAT
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
DNAT tcp -- anywhere 192.168.1.111 tcp dpt:2222 to:10.16.2.2:22
DNAT tcp -- anywhere 192.168.1.111 tcp dpt:2224 to:10.16.1.2:22
iptables -t nat -A PREROUTING -d 192.168.1.111 -p tcp --dport 2222 -j DNAT --to 10.16.2.2:22
iptables -t nat -A PREROUTING -d 192.168.1.111 -p tcp --dport 2224 -j DNAT --to 10.16.1.2:22
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
MASQUERADE all -- anywhere anywhere
iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
</syntaxhighlight>
SQUID proxy - 24/11/16
Configurando iptables para redirecionar as requisições HTTP da rede interna para a porta 3128 do squid:
iptables -t nat -A PREROUTING -i eth1 -p tcp -m tcp --dport 80 -j REDIRECT --to-ports 3128
</syntaxhighlight>
Instalado Squid
apt-get install squid
</syntaxhighlight>
Configuração do Squid
http_port 3128 transparent
acl Sites_Bloqueados url_regex -i "/etc/squid3/sites.txt"
http_access deny Sites_Bloqueados
http_access allow all
</syntaxhighlight>
Criado arquivo com lista de sites
root@ubuntu:/var/log/squid3# cat /etc/squid3/sites.txt
uol
facebook.com
google
</syntaxhighlight>
Restartado serviço
service squid3 restart
</syntaxhighlight>
LOGs das requisições
root@ubuntu:/var/log/squid3# tail -f access.log
1480028587.227 20 172.16.0.2 TCP_DENIED/403 3739 GET http://facebook.com/ - HIER_NONE/- text/html
1480028587.304 1 172.16.0.2 TCP_MEM_HIT/200 13068 GET  - HIER_NONE/- image/png
1480028591.948 21 172.16.0.2 TCP_DENIED/403 3733 GET http://uol.com.br/ - HIER_NONE/- text/html
1480028596.008 179 172.16.0.2 TCP_DENIED/403 3742 GET http://google.com.br/ - HIER_NONE/- text/html
1480028596.106 0 172.16.0.2 TCP_DENIED/403 3743 GET http://google.com.br/favicon.ico - HIER_NONE/- text/html
1480028596.115 0 172.16.0.2 TCP_DENIED/403 3775 GET http://google.com.br/favicon.ico - HIER_NONE/- text/html
1480028602.028 277 172.16.0.2 TCP_MISS/301 866 GET http://terra.com.br/ - HIER_DIRECT/208.84.244.116 text/html
1480028609.735 2427 172.16.0.2 TCP_MISS_ABORTED/000 0 POST http://ocsp.startssl.com/sub/class2/server/ca - HIER_DIRECT/200.143.247.10
</syntaxhighlight>
- HIER_NONE/- image/png
1480028591.948 21 172.16.0.2 TCP_DENIED/403 3733 GET http://uol.com.br/ - HIER_NONE/- text/html
1480028596.008 179 172.16.0.2 TCP_DENIED/403 3742 GET http://google.com.br/ - HIER_NONE/- text/html
1480028596.106 0 172.16.0.2 TCP_DENIED/403 3743 GET http://google.com.br/favicon.ico - HIER_NONE/- text/html
1480028596.115 0 172.16.0.2 TCP_DENIED/403 3775 GET http://google.com.br/favicon.ico - HIER_NONE/- text/html
1480028602.028 277 172.16.0.2 TCP_MISS/301 866 GET http://terra.com.br/ - HIER_DIRECT/208.84.244.116 text/html
1480028609.735 2427 172.16.0.2 TCP_MISS_ABORTED/000 0 POST http://ocsp.startssl.com/sub/class2/server/ca - HIER_DIRECT/200.143.247.10
</syntaxhighlight>
Firewall Iptables 01/12/16
root@ubuntu:/etc# cat /etc/firewall
- Generated by iptables-save v1.4.21 on Thu Dec 1 20:44:52 2016
- nat
- PREROUTING ACCEPT [679:73365]
- INPUT ACCEPT [7:1248]
- OUTPUT ACCEPT [300:21822]
- POSTROUTING ACCEPT [92:6507]
-A POSTROUTING -o eth0 -j MASQUERADE
COMMIT
- Completed on Thu Dec 1 20:44:52 2016
- Generated by iptables-save v1.4.21 on Thu Dec 1 20:44:52 2016
- filter
- INPUT DROP [95:23580]
- FORWARD DROP [56:4000]
- OUTPUT ACCEPT [489:72907]
-A INPUT -s 192.168.1.12/32 -p tcp -m tcp --dport 22 -j ACCEPT
-A INPUT -d 192.168.1.12/32 -p tcp -m tcp --sport 22 -j ACCEPT
-A INPUT -s 172.16.0.3/32 -p tcp -m tcp --dport 22 -j ACCEPT
-A INPUT -d 172.16.0.3/32 -p tcp -m tcp --sport 22 -j ACCEPT
-A FORWARD -s 172.16.0.0/24 -d 192.168.1.101/32 -p udp -m udp --dport 53 -j ACCEPT
-A FORWARD -s 192.168.1.101/32 -d 172.16.0.0/24 -p udp -m udp --sport 53 -j ACCEPT
-A FORWARD -s 192.168.1.101/32 -d 172.16.0.2/32 -p tcp -m tcp --sport 22 -j ACCEPT
-A FORWARD -s 172.16.0.2/32 -d 192.168.1.101/32 -p tcp -m tcp --dport 22 -j ACCEPT
-A FORWARD -s 192.168.1.101/32 -d 172.16.0.2/32 -p tcp -m tcp --sport 80 -j ACCEPT
-A FORWARD -s 172.16.0.2/32 -d 192.168.1.101/32 -p tcp -m tcp --dport 80 -j ACCEPT
-A FORWARD -s 192.168.1.101/32 -d 172.16.0.2/32 -p tcp -m tcp --sport 443 -j ACCEPT
-A FORWARD -s 172.16.0.2/32 -d 192.168.1.101/32 -p tcp -m tcp --dport 443 -j ACCEPT
-A FORWARD -s 192.168.1.101/32 -d 172.16.0.3/32 -p tcp -m tcp --sport 22 -j ACCEPT
-A FORWARD -s 172.16.0.3/32 -d 192.168.1.101/32 -p tcp -m tcp --dport 22 -j ACCEPT
-A FORWARD -s 192.168.1.101/32 -d 172.16.0.3/32 -p tcp -m tcp --sport 80 -j ACCEPT
-A FORWARD -s 172.16.0.3/32 -d 192.168.1.101/32 -p tcp -m tcp --dport 80 -j ACCEPT
-A FORWARD -s 192.168.1.101/32 -d 172.16.0.3/32 -p tcp -m tcp --sport 443 -j ACCEPT
-A FORWARD -s 172.16.0.3/32 -d 192.168.1.101/32 -p tcp -m tcp --dport 443 -j ACCEPT
-A FORWARD -s 172.16.0.3/32 -p tcp -m tcp --dport 80 -j ACCEPT
-A FORWARD -s 172.16.0.3/32 -p tcp -m tcp --dport 443 -j ACCEPT
-A FORWARD -d 172.16.0.3/32 -p tcp -m tcp --sport 80 -j ACCEPT
-A FORWARD -d 172.16.0.3/32 -p tcp -m tcp --sport 443 -j ACCEPT
-A OUTPUT -p tcp -m tcp --dport 80 -j DROP
-A OUTPUT -p tcp -m tcp --dport 443 -j DROP
COMMIT
- Completed on Thu Dec 1 20:44:52 2016
</syntaxhighlight>